Today’s Electric Power and Energy System is a physical grid that is completed by an emerging information and communication technology (ICT) layer, enabling efficiency gains and new functionalities while simultaneously posing challenges for the power system. It is a combined grid – physical and digital and not a grid where one replaces the other: this is why ENTSO-E proposes the term “cyber-physical grid”[1].
This increasing ICT layer will ensure the transition to the next generation power system: smarter, cleaner, secure, more connected and, of course, with the customer as a key player. Information and communication technology (ICT) layer includes various closed-loop control systems to provide reliable and efficient electricity transmission, real-time protection and control functions of the grid. These control systems become attractive targets for cyber-attackers who aim at causing service outage and infrastructural damage. Based on this reality, the SDN-microSENSE project intends to provide a set of secure, privacy-enabled and resilient to cyberattacks tools, thus ensuring the normal operation of EPES as well as the integrity and the confidentiality of communications. In particular, adopting an SDN-based technology, the SDN-microSENSE project will develop a three-layer security architecture, by deploying and implementing risk assessment processes, self-healing capabilities, large-scale distributed detection and prevention mechanisms, as well as an overlay privacy protection framework.
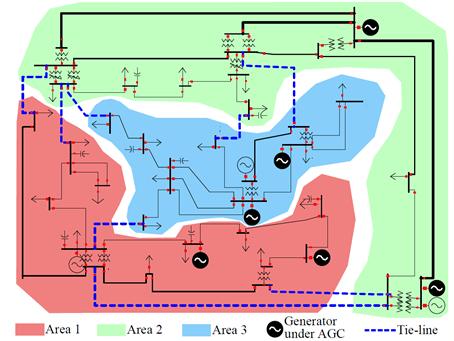
Most of today’s power grids work in large synchronous areas in order to ensure better system operations, reliability and security. Automatic Generation Control (AGC) is a fundamental control system used in all power grids to maintain the grid frequency at its nominal value (50Hz). AGC maintains the grid frequency by adjusting the output power of generators based on measurements collected from sensors distributed in the grid. AGC collects the measurements from remote sensors and sends back generation control commands to the participating generators to restore the frequency to its nominal values and maintain the tie-line power flows between authority areas. A transmission line connecting two buses belonging to two areas is called a tie-line. Fig. 1 illustrates a three-area grid ( dotted lines represent the tie-lines).
AGC is a secondary control system that tunes the setpoints of generators primary control systems to maintain the grid frequency. The grid frequency under AGC control is a safety-critical global parameter of the grid. A frequency deviation caused by an attack will propagate to the entire grid and trigger remedial actions such as disconnecting generators or customer loads. Such unscheduled actions may cause equipment damage and cascading failure.
False Data Injenction (FDI) attack
Recent high-profile intrusions such as Stuxnet has alerted to a general class of integrity attacks called false data injection (FDI). The Stuxnet worm attacked nuclear centrifuges by injecting false control commands and forging normal system states. Its design and architecture are not domain-specific; they could be readily customized against other systems like power grids [2]. By replacing the original measurements with an ‘optimal attack sequence’, the malicious attackers can disrupt the system frequency in the shortest time without triggering certain pre-defined data quality alarms.
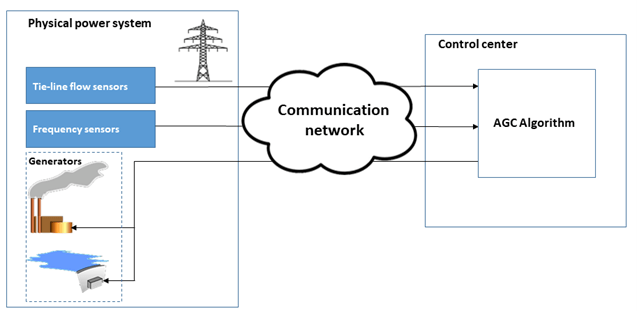
In power grids, the real-time data for AGC is transmitted using telecommunication network, which may provide convenient venues for cyber-attackers to launch attacks. Fig. 2 represents the basic diagram of AGC.
Attack model
In this article, we focus on a general class of FDI attacks on the power flow sensor measurement vector, which can be achieved by compromising sensors data, communication links, and data processing programs at the control center. Hacking geographically distributed physical sensors is tedious and hard to coordinate. Although compromising computer programs at the strongly protected control center is not impossible given existing similar attacks, targeting the communication sensor data links may pose a lower bar for the attacker. Power grids often use network infrastructures which are not secured enough and also use leased lines from third party service providers for communication lines with external substations or distribution companies. Even setting up virtual private networks (VPNs) as logically isolated channels to collect data from the distributed RTUs cannot guarantee security, because of pervasive software vulnerabilities. For instance, by exploiting the Heartbleed bug, the attacker may be able to obtain uninterrupted read and write access to a data links protected by SSL/TLS. The attacker can also launch stepping stone attacks and compromise the VPN software providers. With these abilities, the attacker can mount the attack at a few central spots of the communication network to tamper with the data from many sensors [3].
Pilot simulations
During the pilot it will be assumed that the attacker has read and write access to the power flow measurements. The attacker’s objective is to cause unsafe frequency deviations. As the grid frequency is a safety-critical global parameter of the grid, an unsafe frequency deviation caused by the attack will propagate to the entire grid and trigger remedial actions such as disconnecting generators or customer loads.
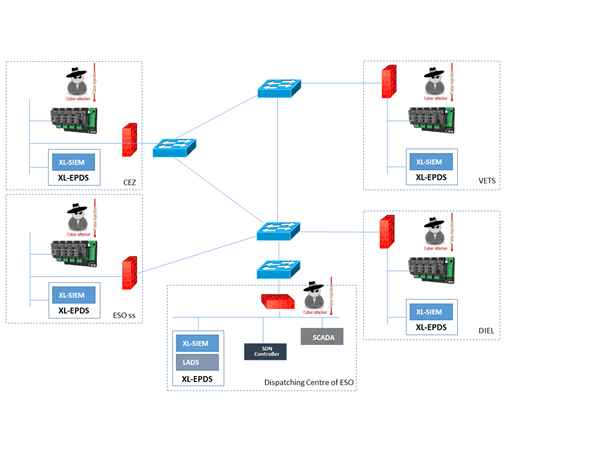
The SDN microSENSE platform will be deployed in five sites. Then massive false data injection attack will be launched concurrently in all domains against the Dispatching Centre of ESO, as fig. 3 illustrates. The attack will target the data integrity of the analogue or status measurements from the RTUs to the control centre. XL-EPDS, the main component of the SDN MicroSENSE paltform will be deployed in the Dispatching Centre of ESO, while instances of the XL-EPDS will be deployed in the other four sites. The pilot will take place in two steps.
During the first step will be simulated the massive false data injection in a whole energy value chain sandboxing environment using an HIL simulation platform. By these simulation scenarios, the SDN-microSENSE platform will be validated in terms of accuracy (anomaly detection assessment), efficiency (anomaly detection time) and effectiveness (accuracy on detecting the real threats).
Then the SDN-microSENSE platform will be validated in dry-run scenarios in the operational environment of the Bulgarian grid operators.
XL-SIEM, ultrafast logging tool for real time collection and analysis of security events, will capture the log files, the events and the traces of the attack in a distributed fashion. XL-SIEM is part of the main component XL-EPDS All recorded traces will be also sent to the National Dispatching Centre of ESO, where the full version of the XL-EPDS is deployed. The L-ADS component will analyse the received data using big data correlations [5]
Conclusion
This article presents a new class of attack, called false data injection (FDI) attack, against power grids. A successful cyberattack could be constructed based on eavesdropped sensor data and a modest amount of prior knowledge about the grid. Then the attacker can systematically and efficiently construct attack vectors, by computing the optimal attack sequence to minimize the remaining time before the grid must initiate costly and disruptive remedial actions such as disconnecting generators and customer loads.
The critical nature of AGC highlights the importance of making it secure to the power grid operation. While communication is the key to a smarter power grid, developing and securing the appropriate cyber infrastructures and their communication protocols is crucial.
References
- The Cyber Physical System for the Energy Transition Digitalisation Challenges, Opportunities and Projects from TSOs and ENTSO-E
- Karnouskos, “Stuxnet worm impact on industrial cyber-physicalsystem security,” in IECON 2011-37th Annual Conference on IEEEIndustrial Electronics Society, 2011.
- Rui Tan, Member, IEEE, Hoang Hai Nguyen, Eddy. Y. S. Foo, Student Member, IEEE, David K. Y. Yau, Senior Member, IEEE, Zbigniew Kalbarczyk, Member, IEEE, Ravishankar K. Iyer, Fellow, IEEE, Hoay Beng Gooi, Senior Member, Modeling and Mitigating Impact of False DataInjection Attacks on Automatic Generation Control
- Jung, O., Smith, P., Magin, J. and Reuter, L. Anomaly Detection in Smart Grids based on Software Defined Networks. Proceedings of the 8th International Conference on Smart Cities and Green ICT Systems (SMARTGREENS 2019), p.157-164.
- SDN MicroSENSE Project. Horizons-EU 2020. 2019.
- Gonzalez-Granadillo G., Gonzalez-Zarzosa S. and Faiella M. Towards an Enhanced Security Data Analytic Platform. 15th International Joint Conference on Security and Cryptography (2018).
- DiscØvery-CyberLens Software Tool. Availale: https://github.com/CyberLens/Discovery. Last accessed 2020.
